The 10 Latest Software Security Trends
Since March 2020, IT professionals have been working from home instead of the office to manage a large workforce. This is because more people are using the cloud (the effect of the pandemic). This first delay was needed so that the focus could be shifted to improving the cloud landscape and building organizational workflows that fit the new normal. Software security has become more important in recent years because of this exploration. So let’s find out the 10 most recent trends in software security right now.
Understanding Software Security
People might wonder, “What’s the big deal about software security?” In the past, people usually had official documents that only they or a small group of people could access. Now, if you don’t protect your documents and use the cloud, a third party could look at all of them. So, we need new software security trends like better app security tools, protection for devices that can connect to the Internet of Things (IoT), and scaling security tools to the cloud.
The software development life cycle (SDLC) framework for making high-quality software in a methodic way that is easy on the budget.
What is Software Security?

In the realm of software security trends, it’s crucial to understand what software security itself entails. Software security focuses on safeguarding computer programs and systems from potential threats. These threats can include hackers, viruses, and other malicious entities.
To achieve software security, developers implement various protective measures. These measures aim to identify and address vulnerabilities within the software. By doing so, software security aims to prevent unauthorized access, data breaches, and system compromises.
One fundamental aspect of software security is authentication. This involves verifying the identity of users and ensuring that only authorized individuals gain access to the software or system. Strong passwords, biometrics, and multi-factor authentication are common methods.
Encryption is another vital component. It scrambles data to make it unreadable to anyone without the decryption key. This ensures that even if unauthorized parties gain access, they cannot make sense of the information.
Regular updates and patch management play a crucial role too. Keeping software up-to-date helps address known vulnerabilities and enhances overall security.
Firewalls serve as a protective barrier, monitoring incoming and outgoing network traffic to block potential threats. Intrusion detection systems further enhance security by identifying suspicious activities and alerting administrators.
Software security is not static; it’s an ongoing process that evolves with technology and emerging threats. Understanding these basics is essential to appreciate the latest software security trends in the rapidly changing digital landscape.
Why is Software Security Crucial in Today’s Technology Landscape?

In today’s ever-evolving technology landscape, understanding software security is not just a choice; it’s a necessity. According to Statista, software security will reach a global value of $7.4 billion by 2024. This figure then continues to increase by 12.89% annually in the next five years.
So, why is software security that important? The answer is quite straightforward; it’s to “avoid unexpected risks and consequences of insecure online activities.”
These risks refer to a wide range of the following things:
Data Breaches: When software security falls short, data breaches become a looming threat. Hackers can steal sensitive information, resulting in devastating consequences for both businesses and individuals. These breaches often lead to substantial financial losses.
Reputation Damage: A breach not only affects finances but also tarnishes an organization’s reputation. Customers and partners lose trust, which can be challenging to regain. Negative media coverage amplifies the damage.
Legal and Regulatory Troubles: Ignoring cybersecurity can lead to fines and legal issues, especially for regulated industries. Regulations like GDPR demand strict data protection measures, and non-compliance can have severe consequences.
Stress and Anxiety: Inadequate security practices create a stressful environment within an organization. Employees constantly worry about potential security breaches, impacting their productivity and well-being.
Unwanted Access: Unauthorized access to digital assets often stems from poor security controls. Misconfigurations, lack of security education, and an “it won’t happen to us” attitude contribute to unauthorized entry.
Exploitable Vulnerabilities: Failing to update software leaves systems vulnerable. Attackers can exploit known weaknesses to gain access, steal data, launch attacks, or even take control of critical systems.
Understanding these risks highlights the critical need for organizations to prioritize software security in line with the latest trends. It’s not just about technology; it’s about safeguarding reputation, finances, and peace of mind.
The 10 Software Security Trends in 2024

Here are ten upcoming software security trends that will cover most of 2024.
1. Cloud Adoption
Today, software development teams have to keep up with application development in the cloud. It’s no longer an option to drag codes and fix vulnerabilities. This gives people who want to break into the system a chance to do so.
In other words, threat actors are increasingly targeting cloud apps and on-premises systems. Even the National Security Agency warned cloud platform users about the potential risks from third-party interventions, which may threaten their on-premises networks.
Many organizations have adopted robust security protocols to safeguard their data storage and business operations on the cloud. However, vulnerabilities still appear because of phishing attacks, malicious software, or even human errors.
To deal with cloud security challenges, application security tools (e.g., Veracode, Synk, or Checkmarx) are added to the toolchain. These tools support developers in detecting, analyzing, and fixing potential security issues promptly. Further, technologies like CSPM or CASB help identify and resolve misconfiguration, unauthorized access, and even compliance risks.
Further, using strong security measures (e.g., encryption or authentication) and continuously updating cloud platforms are still crucial to protect sensitive data and reduce risks.
FURTHER READING: |
1. Web Application Security: The Best Guide and Its Practices |
2. 10 Common Web Security Threats Businesses Might Face |
3. What Is Cloud Security and Cloud Computing Security Defined? |
2. Infrastructure-as-Code (IaC)
Many developers use infrastructure-as-code environments because they are flexible and efficient. But this sudden change has introduced a lot of security holes that attackers are actively exploiting.
How? One of the main risks come from the automation and speed of these environments. Although they allow developers to set up and deploy resources (e.g., servers or networking components) quickly, they sometimes can bypass rigorous checks and balances. If settings are misconfigured, significant vulnerabilities can easily arise and make these environments prone to attacks.
Additionally, IaC has the decentralized nature. This means developers meet difficulty controlling the entire environment all the time. So, it’s no wonder that detecting and reacting to security incidents become more challenging than ever.
To resolve these problems, there will be a big focus on cloud security training, thorough security testing, robust access controls, and continuous monitoring. All these practices help the remote workforce make full use of IaC while mitigating relevant risks.
3. Open-Source Susceptibility
In 2024, there will still be threats to open source. Every week, a company gets a batch of malicious open-source code. Everyone in the organization knows that open-source components need protection because they make it easier for attackers to get into the system.
Existing solutions help developers get rid of the vulnerable package, but they can’t see when attackers drag bad code into containers. This is a security risk that needs fixing by 2024.
It is best to stay away from new components and only use open-source ones that have been around for a long time. To offer a truly secure Software development life cycle (SDLC), you need to build a strong infrastructure and put money into software and application security.
4. Cloud-Native Security
Cloud-native security refers to all the practices to protect apps developed from the ground up to work on the cloud.
In 2022, we found that cloud-native security was insufficiently used and the security industry still didn’t understand it. But this year, organizations are beginning to shift their focus to this software security trend.
APIs are considered a key part of cloud-native security. Yet businesses are also investing in other technologies. One study stated that half of global companies rely on cloud-native solutions for data storage and management, followed by code repositories in their production. 26% are also considering serverless architecture like FaaS (Function-as-a-Service).

Many companies also use 85% of AI frameworks to resolve existing problems, typically data analysis and threat detection, on the cloud. Meanwhile, only one-third integrate AI to automate security processes and handle cloud attacks promptly.
Besides, as more companies are deploying cloud platforms, they pay more attention to cybersecurity mesh architecture (CSMA). This concept integrates security tools and controls to centralize the data, hence improving anomaly detection and effective responses.
Despite these advancements, challenges still remain. In fact, many organizations still overlook important aspects of cloud-native security, like identity management. Therefore, continuous improvement in security protocols and ongoing education are needed to handle these issues.
5. IoT Security With 5G
The wide adoption of 5G technology has accelerated the growth of the Internet of Things. However, in addition to enhanced connectivity and bandwidth, 5G makes IoT devices prone to software bugs and external threats. Therefore, this is one of the most serious security trends you should consider in 2024.
To minimize this issue, organizations need to implement robust security measures like encryption and authentication to protect IoT devices from any attack. Further, use secure communication protocols to safeguard data at rest and in transit between the network and devices.
Organizations also should ensure that their IoT devices only deploy trusted software and can be isolated from critical infrastructure to buffer the impact of potential attacks.
Continuous monitoring and updating are encouraged to help the devices always work as expected. If you outsource this process to an external company, allow that partner to fix vulnerabilities and update security features remotely.
6. AI & ML in Software Security
Artificial Intelligence (AI) and Machine Learning (ML) are double-edged swords in software security. On the one hand, hackers are harnessing these cutting-edge technologies to launch attacks. They can generate more persuasive phishing content, discover security holes in your systems, and automate attacks. The development of AI and ML means cyber threats will become more sophisticated.
On the other hand, AI and ML are leveraged to improve software security. Their algorithms can automate several security tasks like scanning for vulnerabilities, managing patches, monitoring networks, and more. With this capability, AI and ML can instantly alert security teams about potential issues and free them up on more complex issues.
Several AI advancements are widely adopted to improve software security capabilities. They include AI for IT Operations (AIOps), extended detection and response (XDR), and security orchestration, automation, and response (SOAR). These techniques help your company detect complex attacks, identify real-time threats, and automatically respond to them without much human intervention.
7. Solutions to Exposed APIs
One of the most common way for hackers to get into your system is through exposed APIs. In the past, there were many cases of bad things happening through APIs that were left open. So, the same threat will happen again in this new year.
The exposed APIs are easy to go after. Organizations need to get up to speed on how to use these programs to their full potential. Attackers will take advantage of the delay, which will force software developers to find ways to make API authentication and authorization strategies more secure.
8. Susceptible Legacy Devices
Cyberattacks will be most likely to target devices that run quietly in the background and are often forgotten.
As cell phones and laptops get older, the companies that make them stop making software updates for that model and only make updates for newer models. This makes them older models that are more likely to be hacked because they are easy for hackers to get into.
Developers of software must keep working to create a safe environment for older devices.
9. Zero Trust Architecture
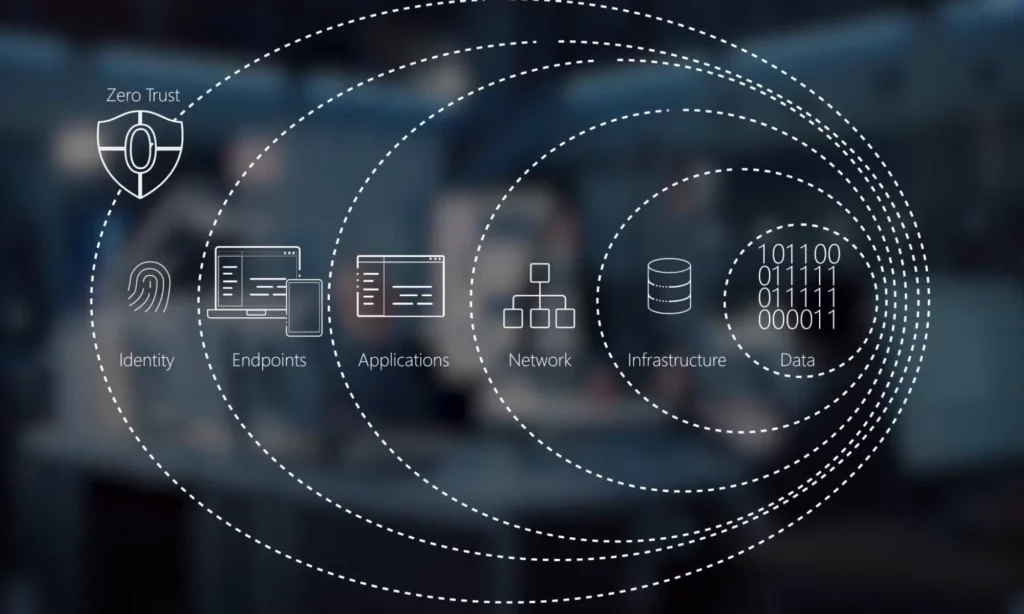
Previously, companies often rely on traditional security perimeter to safeguard their data by isolating the internal network from the external internet. Because of the Covid-19 outbreak, emerging trends like cloud-based devices, remote/hybrid working, and BYOD (Bring-Your-Own-Device) challenged these traditional security approaches.
This led to the wide adoption of Zero-Trust Architecture (ZTA). The security model boasts a principle, “never trust, always verify.” It means every device, application, and user must be validated before being allowed to access resources. This breaks the traditional concept that everything inside the network is secure and anything outside is a threat.
For this reason, ZTA provides a more robust, secure approach to protect your data by limiting access to sensitive information and resources. It also allows remote or hybrid development teams to secure access. Therefore, ZTA is expected to become the future software security trend with a global value of $133 billion by 2032.
10. DevSecOps Integration
This is a software development methodology that incorporates security into the entire SDLC. It ensures security is always a top priority from ideation to launch and ongoing maintenance by combining the DevOps principles with security.
Particularly, development and operations teams are well-trained to have essential security knowledge and skills. They then collaborate with security teams to frequently review code and continuously monitor apps and infrastructure during development.
Further, they also use security testing and automation tools to streamline security tasks (e.g., penetration testing) and minimize human errors while fostering security efficiency. All these practices help them detect potential security threats and react instantly to them.
Enhanced Software Security With Designveloper

These software security trends for 2024 are likely to have an effect on how well organizations meet their security rules. Understanding a high demand for robust security measures, we here at Designveloper offer associated services to help your company systematically produce high-quality software while securing software development.
With over a decade of experience in software development and cybersecurity consultancy, we’re committed to provide full-cycle yet customized services:
- Penetration Testing: We help you conduct a wide range of testing procedures to identify security vulnerabilities. Whether web apps, mobile apps, networks, social engineering, or resolution suggestions, we offer suitable solutions to your specific needs.
- Security Training: Our customizable training programs cover diverse topics. They include secure coding, security awareness, incident response, and threat modeling.
- Security/Privacy Threat Modeling: Threat modeling is a proactive process that helps your company detect possible risks in software development. Our threat modeling services cover software representation, threat identification, mitigation strategies, and evaluation.
- Security Consultancy: We have extensive expertise and experience to guide you how to embed security practices into the software development cycle. We also evaluate your existing security architecture and provide appropriate advice for improvements. Further, we help you understand and adhere to specific industry standards like HIPAA or ISO/IEC 27001.
So, contact us and revolutionize your software security now!