Cloud computing, hybrid work, social media, and new applications have expanded the IT landscape, making businesses more exposed to cyberattacks. A damaging breach can stem from an employee’s seemingly innocuous Facebook or Instagram post. How does a company protect itself from cyber threats? One way is through secure software development. This approach ensures that from the very first line of code, software is built to protect user data and sensitive company information.
Secure software development
With a secure software development approach, developers prioritize security from the start and maintain it through every stage of development until deployment. The aim is to develop software systems that are secure and robust against malicious attacks and guarantee data privacy.
Secure software systems have become non-negotiable. Software vulnerabilities give cybercriminals an open door to launch attacks and steal data, often for financial gain. Even more concerning is the damage these attacks can cause to public systems like infrastructure, transportation, and healthcare.
Counting on Software
User trust is directly tied to data security and software reliability. Software that performs flawlessly every time fosters trust in the growing role of software in all aspects of life. Society depends and counts on secure and reliable software, and when this expectation is breached, the fallout can be devastating.

Breaking User Trust
In 2020, Russian operatives hacked the IT services provider Solarwinds. Multiple government agencies and businesses used the software tool at the time and downloaded the corrupted software. The resulting massive breach exposed sensitive government and corporate data, placing a question mark over the trustworthiness of these organizations’ security software.

Protected by blockchain technology, cryptocurrencies are vetted as unreachable. Yet, hackers have gotten away with billions in cryptocurrencies. This vulnerability prevents mainstream adoption of digital currencies because the average person doesn’t trust them.
Integrating Virtual Privacy Network (VPN)
A reliable VPN provider is one of the best auxiliary tools to enhance cybersecurity. Software developers can integrate VPN-related solutions or concepts to improve their security features. Here are some suggestions.
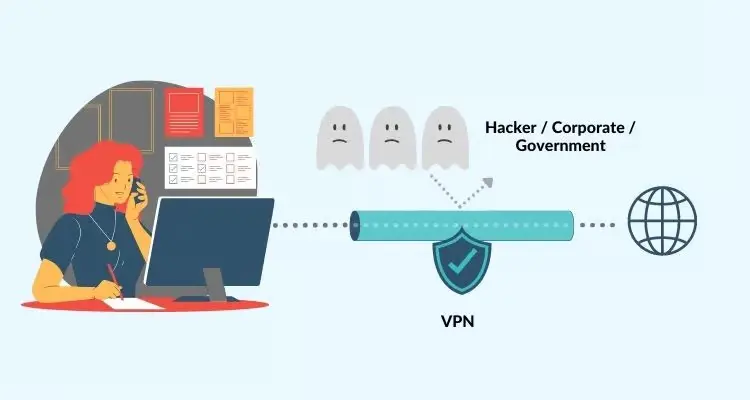
- Developers can add VPN features to their software to create encrypted connections and keep data secure.
- When developing software for streaming services or global communication platforms, it’s useful to incorporate VPN features like IP masking to enable geo-restricted content and support users who want to protect their privacy.
- Developers can use APIs provided by VPN providers and integrate them with their applications, ensuring smooth VPN connections without the need for a separate VPN app.
- Encrypted data can be transmitted using various VPN protocols, securing data transmission within the software. This is an ideal approach for financial or healthcare apps that house sensitive user data.
- With VPN-integrated software, remote employees can securely access company resources.
- Developers selling apps can build trust by adding VPN solutions, showing they care about user privacy and security.
Best Practices for Secure Software Development
To build software that users can trust, developers should follow these best practices for secure development.

- Code security into software from the start. View security as a fundamental part of software design, not something that developers can add later.
- Limit access to authorized users only. Developers can also use role-based control in addition to authentication and authorization protocols.
- Use a multi-layered defense strategy. This way, if one security layer fails, others will still protect the system. Examples include firewalls, access controls, secure coding, encryption, and more.
- Make secure coding best practices such as input validation, encrypted communications, and creating multiple security layers a common habit.
- Implement all software updates immediately so your system is not vulnerable to breaches.
- Practice continuous monitoring. Continuous vigilance ensures that someone notices a breach as it happens. The sooner someone discovers a threat, the faster the company can take action.
- Use automated compliance monitoring. All software development must follow the General Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standard (PCI DSS) guidelines. The GDPR and the PCI DSS are measures to protect personal data privacy. The best way to ensure continuous compliance is for organizations to use an automation tool to monitor compliance.
Ongoing Security Awareness Training
Organizations can offer ongoing security training to maintain long-term security. Keeping the development team updated on the latest threats helps them prioritize security in their work.
Cybercrime and those who perpetrate it may be old news, but they are not dead and buried. They are a growing threat. Organizations and their software developers can’t afford to be ignorant of the facts. Ongoing education for developers on emerging security threats remains crucial.
Spreading security awareness in development teams and collaborating with reliable security partners will lead to resilient and secure software that will earn user trust.
Conclusion
At Designveloper, we firmly believe that secure software development is not just a best practice, but a critical responsibility for every developer and organization. By prioritizing security throughout the entire software lifecycle—from design to deployment—companies can protect their data, maintain user trust, and prevent costly breaches. We understand that implementing security may seem daunting, but with the right approach and a proactive mindset, it becomes an essential part of creating reliable, resilient, and trustworthy software. We encourage all developers to integrate security into their daily workflow and to view it as an ongoing commitment, not just a one-time effort. Together, we can build a safer digital world.






Read more topics