It’s not enough to just have a good app. You also need to make sure that it’s secure from hackers and viruses. With a few simple tips, you can protect your business and your customers from a cyber attack. The first step is making sure the app is encrypted. This means that no one can get in without the right password or access code. Next, you’ll want to make sure the app stores passwords securely and protects personal information like credit cards. To learn more about how to keep your app safe, read on! Let’s deep down in this blog post about app security for your business!
What Is App Security?
App security involves controlling and protecting an application’s use by users. It includes all aspects of the application lifecycle (from design to support), from configuring and using the web and mobile devices to implementing data security, monitoring, and monitoring web or mobile applications.
Although app security is a set of methods and tools, it is particularly useful for securing mobile applications. Mobile apps tend to have more defects in them compared to web applications, due to the use of non-standard features.
Mobile applications are more prone to security threats, due to their small processing space, smaller screens, and real-time nature.
Most mobile applications also have complex user interfaces, often referred to as interfaces that contain both information and functions.
FURTHER READING: |
1. Native Mobile App Development: Why Your Business Need It? |
2. The 15 Best Languages for App Development in 2025 |
3. 5 Mobile App Development Frameworks You Should Consider |
What Are the Common Types of App Security Threats?

Malicious hackers use various methods to attack mobile applications. Most of these threats generally come into four categories:
- Data theft. This is one of the most common types of app security threats.
- Phishing attacks. This threat involves the theft of data or information via fraudulent websites or emails.
- Attack vectors. Attack vectors can be classified into two types — man-in-the-middle attacks and transparent attacks.
- Web application attacks. The target of these attacks are apps that use HTTP/2, HTTPS, ASP, and AJAX protocols.
Which are the major threats associated with web app security?
Malicious hackers commonly create fake websites that mimic well-known websites such as Facebook, Twitter, Airbnb, and others.
Type of Attack
Besides common vulnerabilities, web applications are also exposed to large-scale threats, which require the prevention of certain actions and cross-site scripting (XSS) and clickjacking, among others. Cross-site scripting (XSS) is a type of vulnerability that allows attackers to inject malicious code into the input fields in web forms. This surprisingly causes most of the application security issues.
Examples of a web application security flaw include <script> var ctrlKey = document.getElementById(“user1”); /* javascript */ // <script>document.querySelector(“input1”).valueOf.push(“user1”); /* js */
Prevention Tips

Considering the scope of the problem, organizations are left with no option but to invest heavily in securing their web applications. However, deploying an application-layer security layer like Application Whitelisting can be a prohibitively expensive proposition, considering the real-time nature of application security scanning.
There are several tools in the market that can help you build and deploy a good Application Security Scanning solution. Some of the popular tools are listed below.
Recommended reading: 15 Mobile App Development Trends That Lead the Software Industry
Important Security Measures to Take

Most of the security risks associated with web and mobile applications can be addressed by following the following precautions:
1. Put up a good online presence
The first thing you should do in order to protect your business is building a solid online presence by creating a website for your company. For example, if your online business is selling magazines, then you should have a reputable website (meaning it has a great design and offers informative information) and must not make it easy for hackers to access its database.
2. Perform background security checks
You should conduct background security checks on your application before developing it.
How to Detect Application Vulnerabilities?
The process of software security assessment begins with identifying vulnerabilities in an application and mapping them to known attack scenarios. The application security practitioner will then analyze the application’s code and create a list of flaws that may compromise application.
Following are the primary and secondary application vulnerabilities that can lead to application compromise:
- Remote code execution (RCE): Code execution vulnerability allows an attacker to execute code in the context of the operating system and with the privileges of the user running the application.
- Trusted source: This security risk occurs when an attacker can gain privileged access to the application and execute malicious code without the need to establish a TCP connection.
Security Checklist for Developers
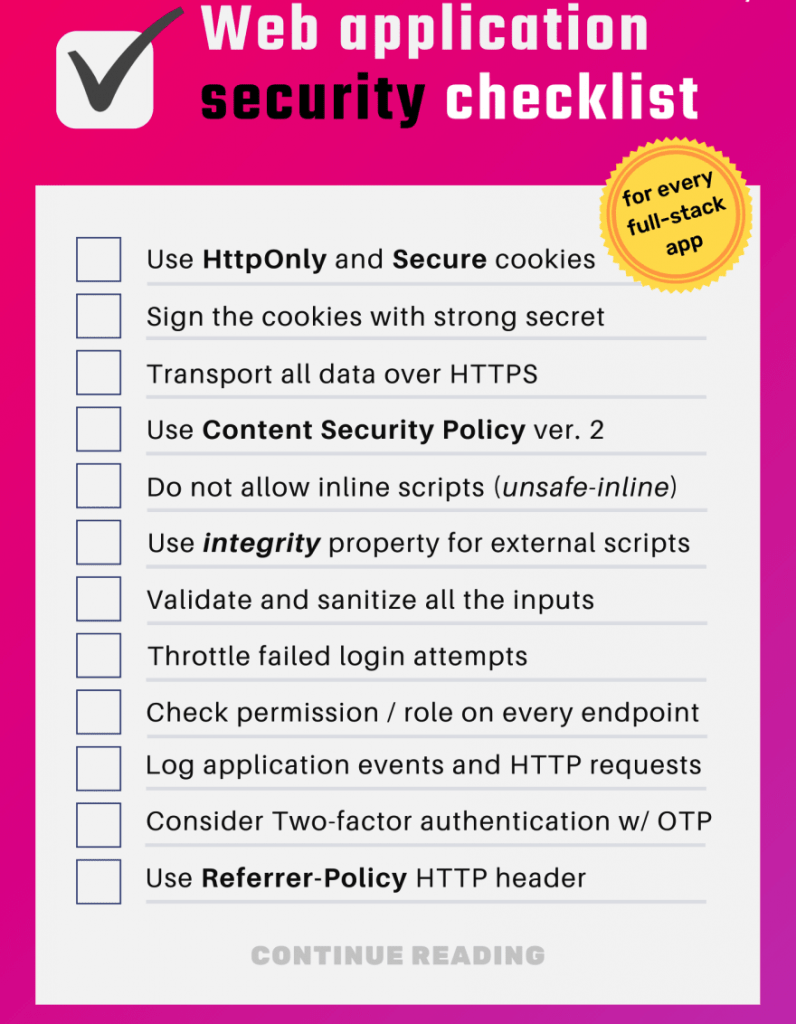
An application security checklist can help secure an app from attacks and vulnerabilities. But how to go about writing application security guidelines, in practice?
Applications are vulnerable to two main kinds of threats. These attacks consist of potential or actual security weaknesses in an application. These security vulnerabilities can be caused by sloppy coding and maintenance, as well as a lack of sufficient security measures in the application.
- AUTHENTICATION SYSTEMS (Signup/Signin/2 Factor/Password reset)
- USER DATA & AUTHORIZATION
- ANDROID / IOS APP
- SECURITY HEADERS & CONFIGURATIONS
- SANITIZATION OF INPUT
- OPERATIONS
- PEOPLE
Conclusion
Digital security is paramount in today’s society, with so many apps and devices demanding our data and passwords. With more than 1 billion people joining the internet every year, cyber-attacks are becoming more frequent.
Whether you are an IT professional or just someone who has a smartphone, it is important to know how to keep your data safe. At the most basic level, all you need to do is password-protect your device. But there are many other steps you can take to ensure that only the people who are authorized have access to your private information.
We know it isn’t easy to make the right choice, but we at Designveloper are here to help you. We offer a wide range of services from web development and mobile application to business consulting. Tell us now for free estimations! Don’t hesitate to contact us now if you want to upgrade your business with this latest technology.






Read more topics